Automating updates: configuring unattended-upgrades on Debian 12
18 Jun 2025, 17:28:03
One of the basic security rules on dedicated and virtual servers is to keep the software up to date. This is precisely the rule that most users often disregard. We will try to fix this in this article, specifically by looking at a tool that will allow your VPS or dedicated server running Debian 12 (and not only) to install important security updates automatically: unattended‑upgrades. On some operating systems, such as Ubuntu 22/24, this package is installed and works by default, but in Debian, unattended-upgrades is not included in the pre-installed set of components.Installing and activating unattended‑upgrades
Connect to your server via SSH as root (this is not required, but all subsequent commands will be executed on its behalf) and update the package lists:apt updateInstall unattended-upgrades and its dependencies:
apt install unattended-upgrades apt-listchanges- unattended-upgrades - the automatic update service itself;
- apt-listchanges - shows a list of changes in packages in a letter.
Enable automatic updates:
dpkg-reconfigure --priority=low unattended-upgradesWhen asked "Automatically download and install stable updates?" in the dialog box, select "Yes" and you will receive a notification that a new configuration file has been created.
Configuration of unattended‑upgrades
The main configuration file for unattended-upgrades is located at /etc/apt/apt.conf.d/50unattended-upgrades. Let's open it with the command:nano /etc/apt/apt.conf.d/50unattended-upgradesPay attention to its key section Unattended-Upgrade::Origins-Pattern:
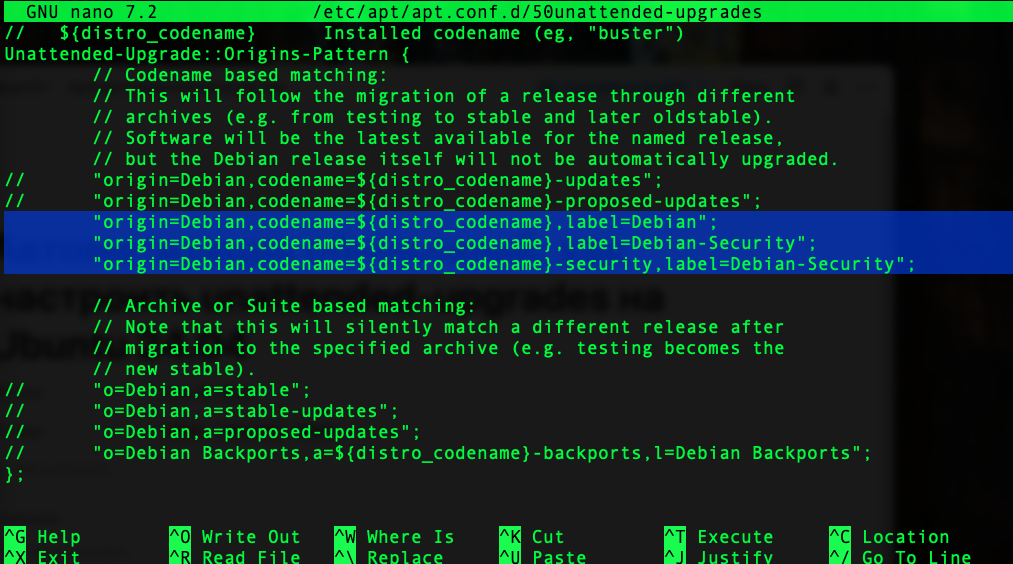
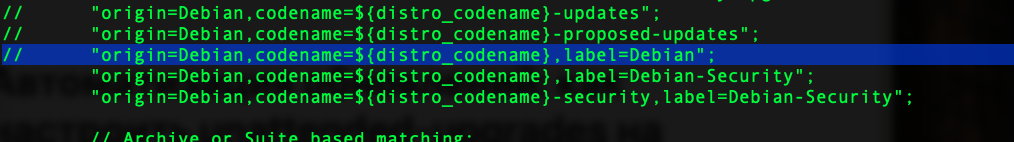
This section of the configuration describes the sources for automatic updates. We see three active sources by default. However, we are only interested in automatically receiving security updates. Let's comment out the entry responsible for updates from the main system repository:
The following useful parameters are Mail and MailReport.
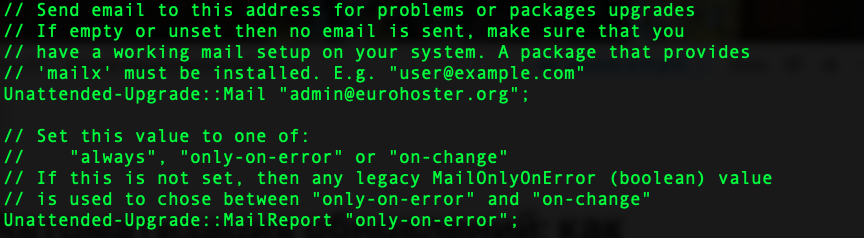
They must be uncommented and filled in. These parameters will help you receive error reports via email if any occur.
- Unattended-Upgrade::Mail "your@email.com"; - your email address;
- Unattended-Upgrade::MailReport "only-on-error" - selecting the notification mode (always, only-on-error, on-change), only-on-error - to send an error report.
Setting up a task schedule
The file /etc/apt/apt.conf.d/20auto-upgrades contains the settings for the automatic update schedule. Let's open it with the command:nano /etc/apt/apt.conf.d/20auto-upgradesThe configuration in this file is optimal for our task by default, but let's take a closer look at it.
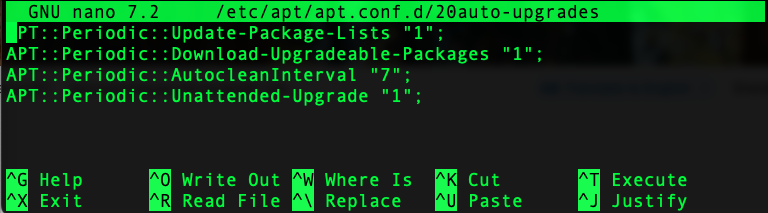
- Update-Package-Lists "1" - update package lists daily;
- Download-Upgradeable-Packages "1" - download new versions daily;
- AutocleanInterval "7" - clear the cache of old packets every 7 days;
- Unattended-Upgrade "1" - run daily unattended‑upgrades.
Test run
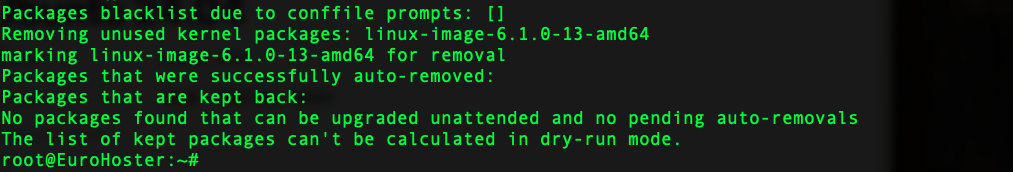
To test the configuration and overall performance of the service, use the following command:unattended-upgrade --dry-run --debug- --dry-run - download update packages (without installation);
- --debug - detailed output for troubleshooting configuration errors.
Starting unattended‑upgrades
Once you have changed the configuration files, you must run the utility manually to check and apply the changes:unattended-upgradeYou won't get any notifications if there aren't any errors in the config.

You can also check the operation of systemd timers responsible for the operation of unattended-upgrade:
systemctl status apt-daily.timer apt-daily-upgrade.timerTheir status should be active.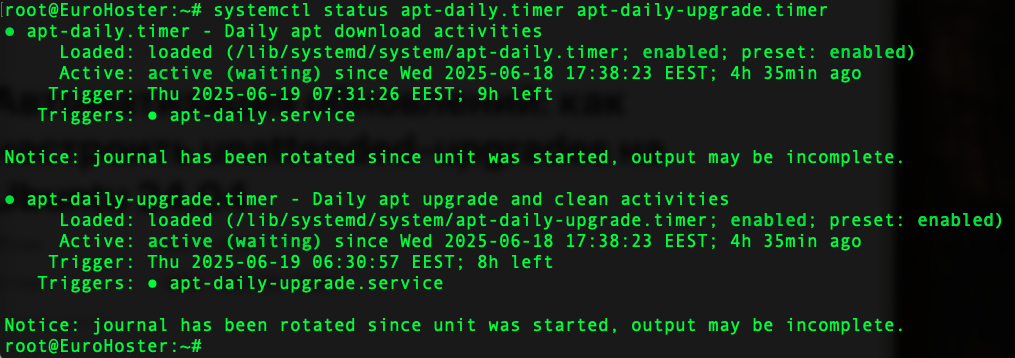
The log file /var/log/unattended-upgrades/unattended-upgrades.log contains all information about the progress of automatic updates.
The example uses a freshly installed system and the software does not need to be updated:
We have thoroughly examined the process of configuring automatic security updates on a dedicated server or VPS running Debian 12. These simple steps will significantly improve the security of your project. If you encounter any problems configuring unattended-upgrade on EuroHoster servers, you can always contact our technical support team via the ticket system or online chat on our website.