How to disable root access via SSH and create a secure user in Ubuntu 24.04
27 Jun 2025, 20:34:37
Disabling remote access to the server for the root user is a basic security measure when using servers with a Linux-based operating system. In general, if you regularly update the root password or disable password authentication and follow other basic security rules, there is nothing wrong with allowing superusers to connect via SSH. This is why, in most cases, when you rent a dedicated server or VPS, you receive this data for authorization on the server. However, as with any other basic case (port 22 for SSH or URL /admin for the site's admin panel), this username is a target for attackers. Another danger of using the root user for everyday tasks is its maximum privileges in the system. Scripts uploaded and executed by this user will have access to all areas of your server.In this article, we will be working on a freshly installed Ubuntu 24.04 OS, but the instructions are also relevant for many other Linux-based systems. We will perform three simple steps: create a new user, grant them sudo privileges, and disable root access via SSH.
Creating a new user
Connect to the server via SSH as root:ssh root@your_server_IP- your_server_IP - Your server's IP address
adduser ehuser- ehuser - your username
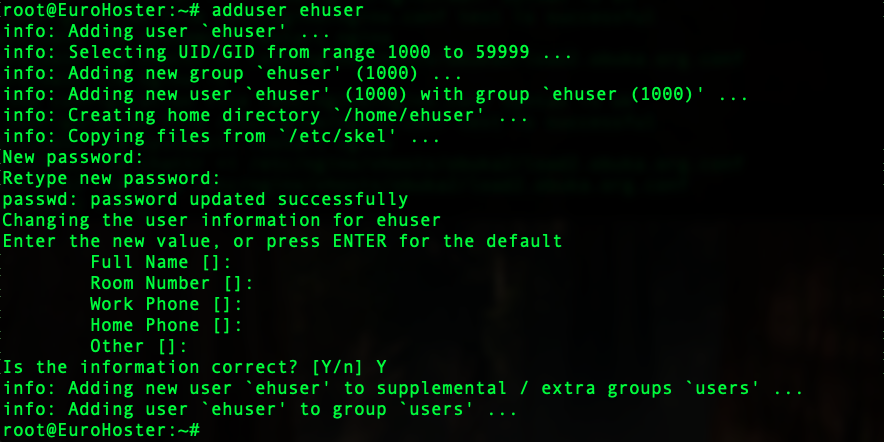
Enabling sudo for a user
We have executed only one command, but we can already connect to the server via SSH under our new user. However, when executing any commands on behalf of the superuser, the familiar sudo utility returns an error - {your_user} is not in the sudoers file.: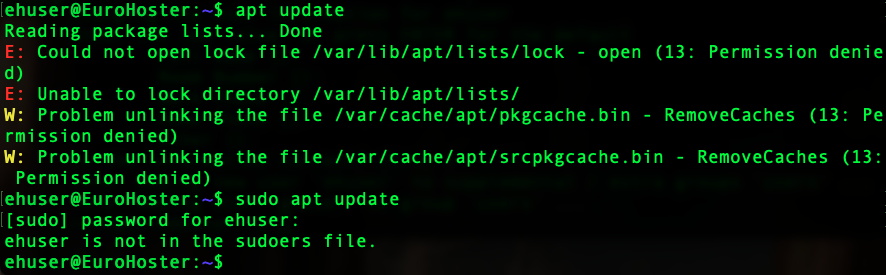
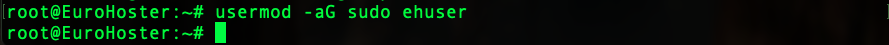
We need to add our new user to the sudo group to fix this. This can be done using the usermod utility:
usermod -aG sudo ehuser- -a - add a user to a group without removing them from other groups;
- -G sudo - specify which group the user should be added to. In our case sudo;
- ehuser - имя вашего пользователя.
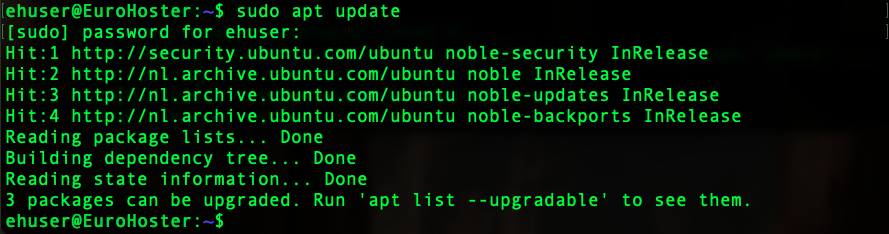
When using sudo under a new user, we are successful this time:
Disabling root access via SSH
To perform the following actions, namely directly disabling SSH access for the root user, we can now connect to the server under a new user and execute all further commands using sudo.Open the SSH settings file:
sudo nano /etc/ssh/sshd_configFind the PermitRootLogin parameter: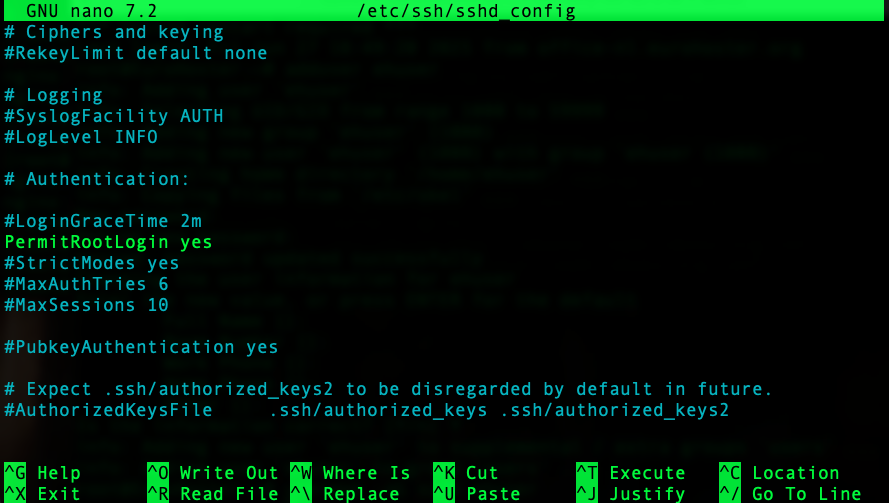
Change yes to no, save the file with Ctrl + O, and exit nano with Ctrl + X.
Restart the SSH server:
sudo systemctl restart ssh.serviceNow, when attempting to connect via SSH as the root user, your server will return an access error: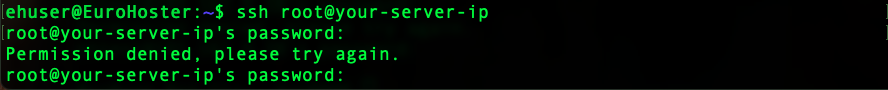
This security practice should only be used in conjunction with other basic practices, such as changing the default SSH port, which we discussed in the article How to Change the SSH Port, and configuring authorization via SSH keys, which is also discussed in the article. Configuring authorization by SSH keys on a Linux server. If you encounter any difficulties implementing these security measures on dedicated servers and VPS from EuroHoster, you can always contact our online chat or ticket system for assistance.