Obtaining a Let's Encrypt SSL certificate in Ubuntu with Certbot
28 Jan 2025, 10:45:09
What is an SSL certificate and why do I need one?
An SSL certificate is a special digital certificate that provides a secure connection between a web server and a user's browser. It encrypts the data transmitted between these two points, which protects it from being intercepted by intruders. The main purpose of an SSL certificate is to ensure the confidentiality and integrity of information, especially when it comes to transmitting personal data such as passwords or payment details. Having an SSL certificate on a website not only increases the level of security, but also has a positive impact on user trust. Modern internet browsers such as Chrome and Firefox mark sites without SSL certificates as insecure, which can scare away potential clients. In addition, search engines like Google favor sites with SSL, which can improve their position in search results. Thus, installing an SSL certificate is not just a security issue, but also an important step to improve the reputation of your online business. In today's environment of data protection and client privacy, it becomes a necessity for every website owner.Advantages of using Let's Encrypt to obtain an SSL certificate
Using Let's Encrypt to obtain an SSL certificate offers many significant advantages that make it an ideal choice for both small website owners and large companies. First, Let's Encrypt provides certificates for free, which significantly reduces the cost of securing your web resource. Secondly, the process of obtaining a certificate is automated, which significantly reduces the time required to install and update it. This is especially important for those who do not have technical skills, as Let's Encrypt offers clear instructions and support for various servers. In addition, automating certificate updates helps avoid expiration issues, which can lead to loss of user trust and negative SEO consequences. Finally, using an SSL certificate from Let's Encrypt helps to increase visitor trust, as the presence of HTTPS protects user data and improves a site's search engine ranking. Thus, Let's Encrypt becomes not only cost-effective but also an effective tool for creating a safe and secure online presence.Installing Certbot on Ubuntu
Installing Certbot on Ubuntu is a key step to ensure your website is securely connected using SSL/TLS certificates. First, make sure your system is up to date by running the commands:apt update
apt upgradeThen install Certbot using the Nginx command for Nginx users:
apt install certbot python3-certbot-nginxAnd for Apache:
apt install certbot python3-certbot-apacheAfter successful installation, you can run Certbot to obtain and install the certificate. To do this, run the command depending on your web server:
certbot --nginxorcertbot --apacheCertbot will prompt you to enter your Email and domain name and will automatically configure your server to work with the obtained certificate. Don't forget to configure automatic certificate renewal by adding the command to cron:
0 0,12 * * * root certbot renew --quiet
This ensures that your certificate will be updated without your intervention. By following these steps, you can easily install Certbot on Ubuntu and secure your website, increasing user trust and improving SEO rankings.
Obtaining an SSL certificate using Certbot for a new domain
To simplify the task of obtaining an SSL certificate with the above command, you can initially set the domains for which certificates will be issued. This will reduce the number of interactive questions of certbot utility:certbot --nginx -d example.com -d www.example.com -n --agree-tos --email admin@example.comwhere example.com should be replaced with your domain.Note that if there is a Nginx configuration at /etc/nginx/sites-enabled/example.com.conf, the certificate parameters will be added to it. And in case of absence of such a file to the default /etc/nginx/sites-enabled/default.
Configuring automatic certificate renewal
Modern web servers such as Apache and Nginx make it easy to integrate automated SSL/TLS certificate renewal processes. For this purpose, it is recommended to use tools such as Certbot, which supports automatic certificate renewal from Let's Encrypt. After installing Certbot, you can configure the task scheduler (cron) to check the certificate expiration date and trigger the renewal 30 days before it expires (the command itself is listed in the article just above). This will eliminate the risk of your site downtime due to an expired certificate. It's also important to remember to test the renewal process: you can use the SSL certificate renewal simulation command to make sure everything is working correctly:certbot renew --dry-runSetting up certificate status notifications helps you stay on top of potential issues. With automatic certificate renewal, you not only maintain a high level of security, but also save time and resources, which is critical for any business in the digital age. Thus, regular certificate renewal becomes part of your strategy to protect data and build client trust.
In modern systems, there is no need to add a cron job, as there is a Certbot.timer service to automate the SSL certificate renewal process. Its main task is to periodically check and renew certificates, thus avoiding their expiration and guaranteeing the security of your website. Using certbot.timer is especially relevant for administrators who encounter common certificate errors such as expiration or misconfiguration. The jobs run automatically through the systemd system scheduler. Certbot.timer will perform certificate validation and if the certificates are nearing expiration, it will automatically initiate the renewal process. This significantly reduces the burden on administrators and allows them to focus on other critical tasks.
You can check the operation of the Certbot timer with the command:
systemctl status certbot.timer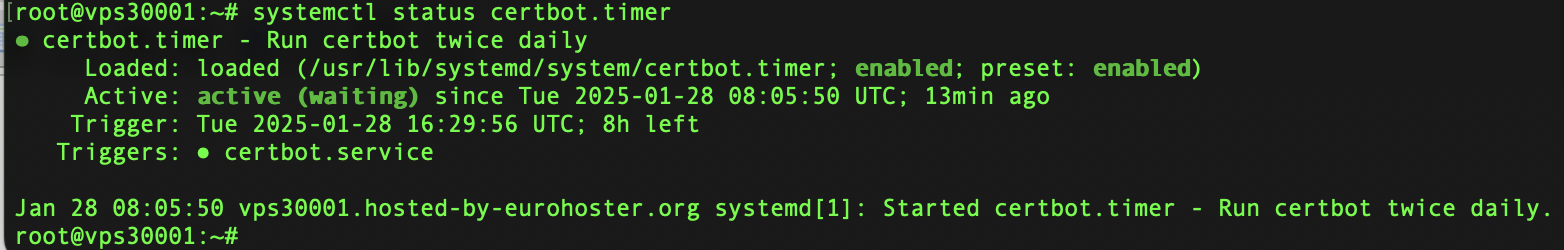
In this output you can see that the service will run the job twice a day, the last run was 13 minutes ago and the next one is still 8 hours away.
Configuring the ufw firewall
If you are using a firewall, don't forget to open access for port 443 to allow sites to run over a secure connection. Below I will describe how to do this in the case of using ufw firewall in Ubuntu.The current ufw firewall settings can be viewed as follows:
ufw status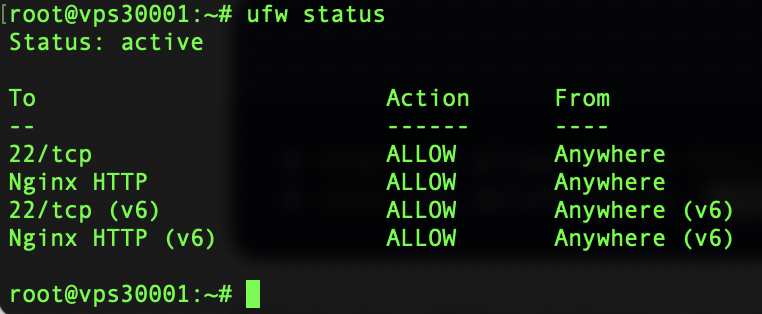
Allow both HTTP and HTTPS traffic. The easiest way to do this is to activate the Nginx Full profile, while removing Nginx HTTP:
ufw allow 'Nginx Full'
ufw delete allow 'Nginx HTTP'And double-check the status.
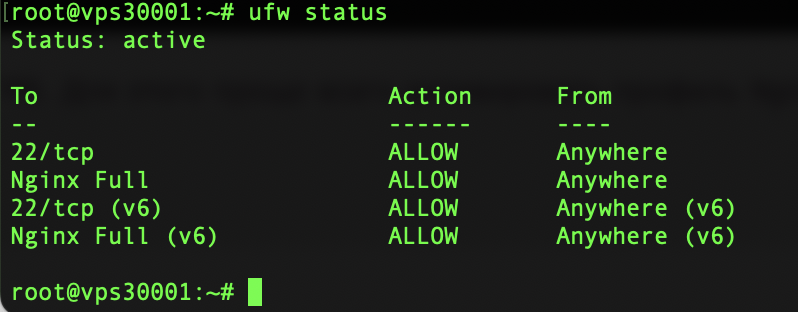
This completes the configuration of Certbot.